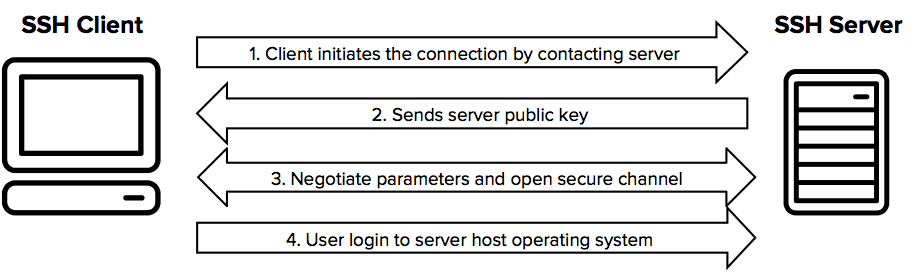
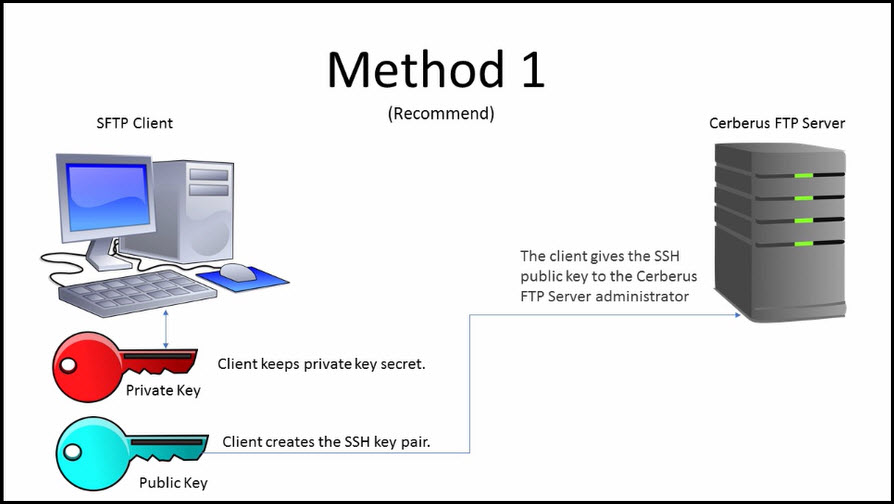
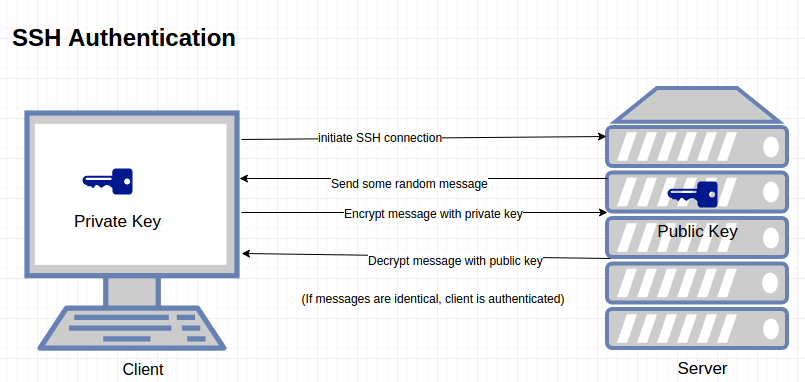
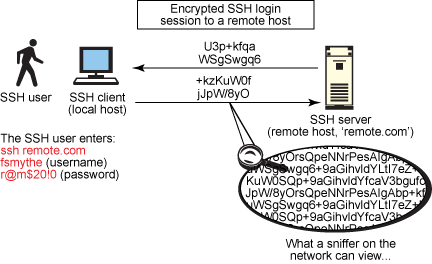
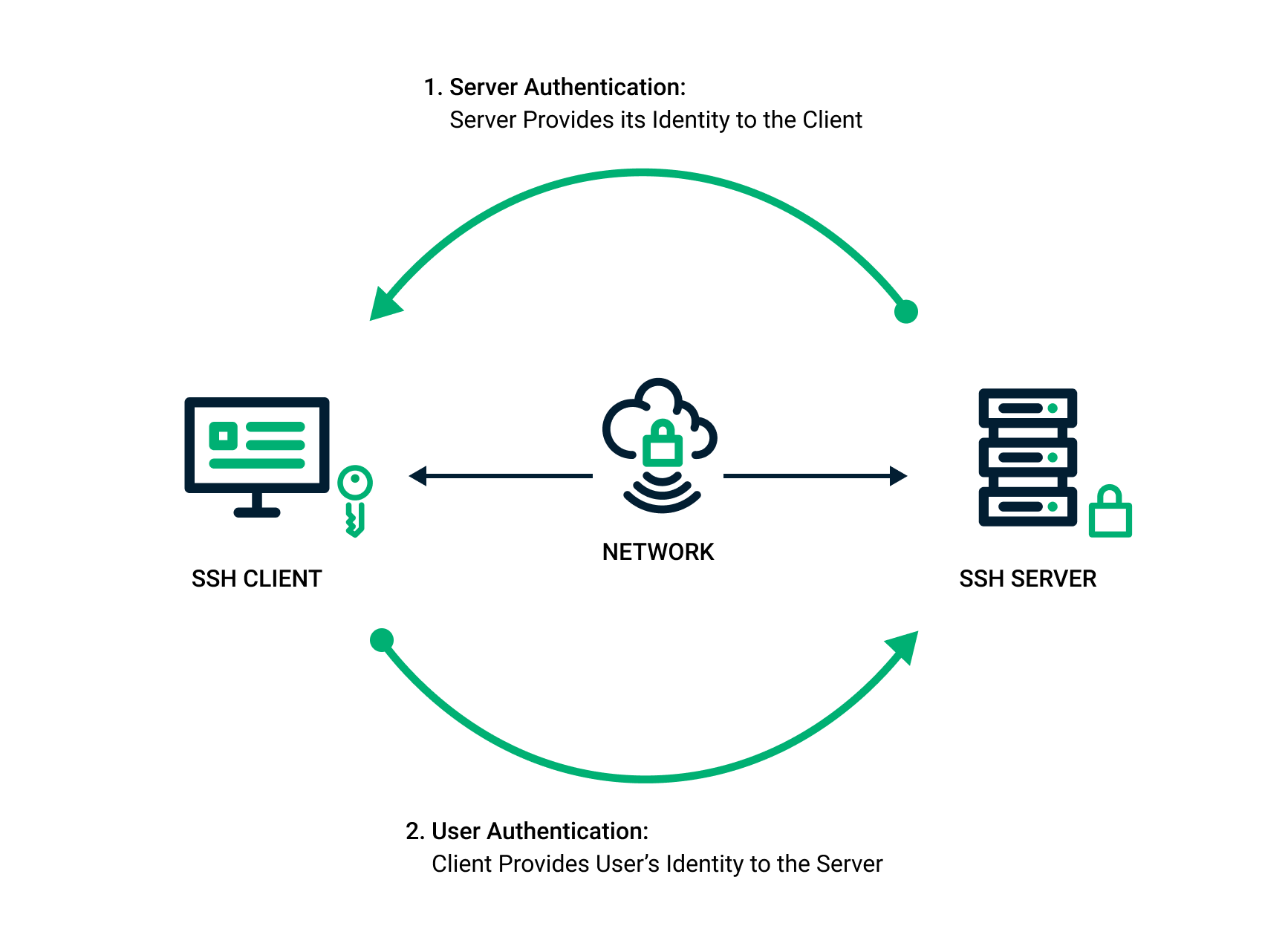
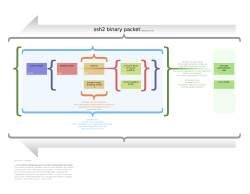
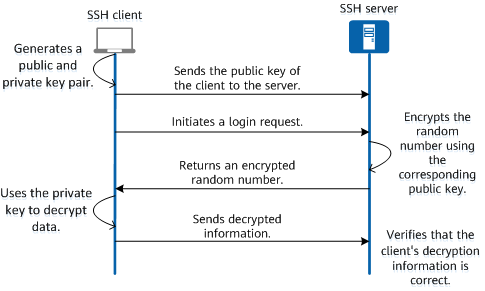
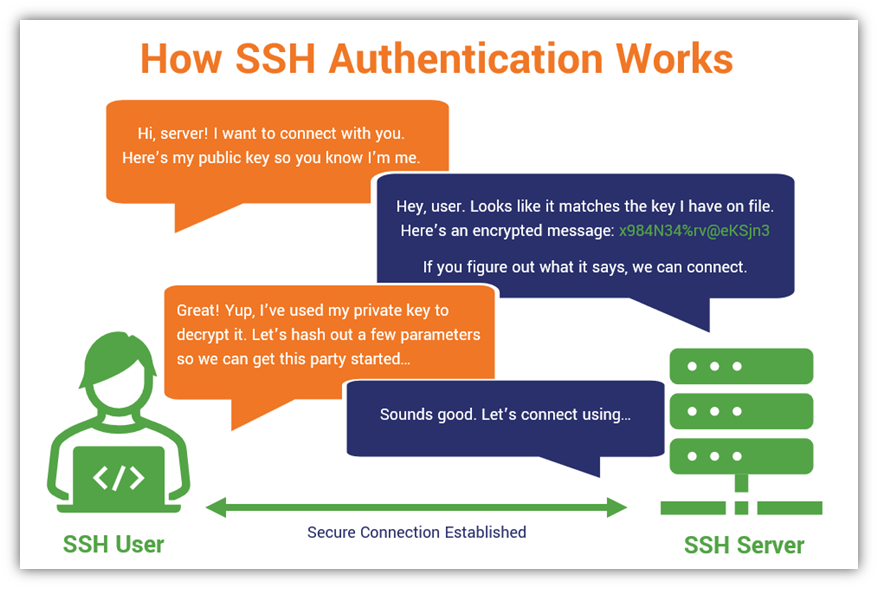
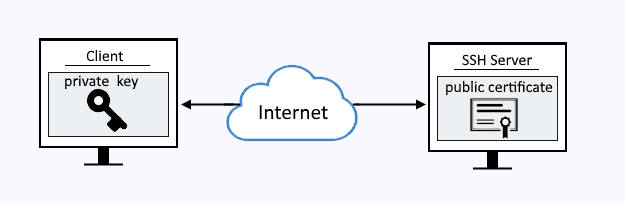
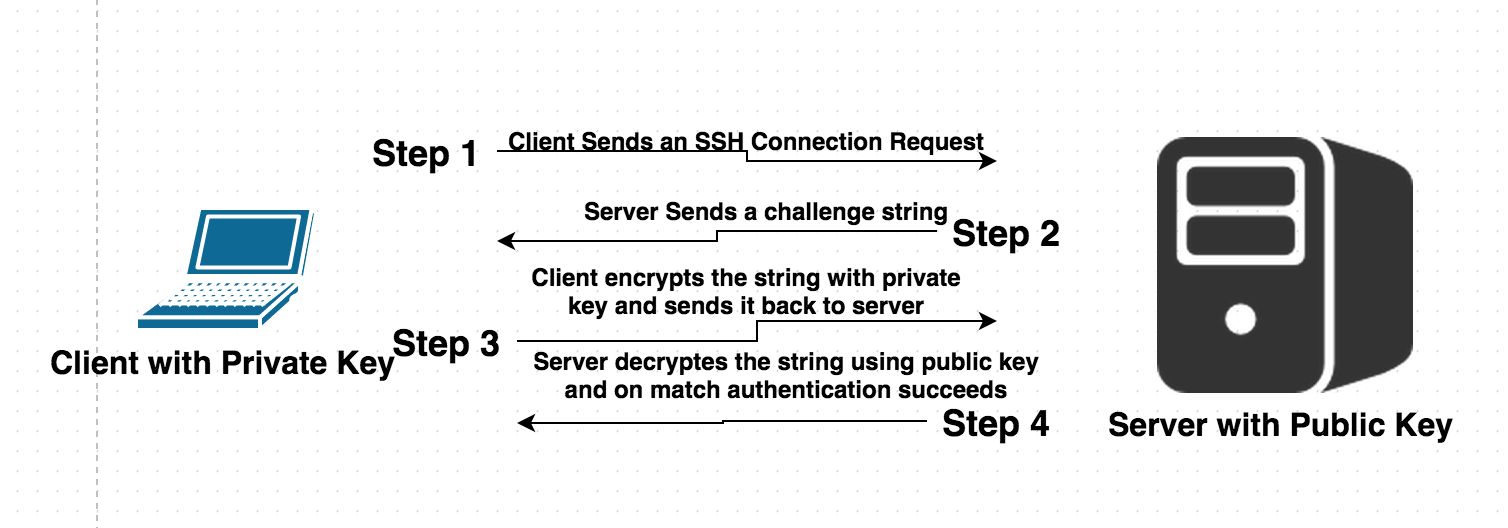
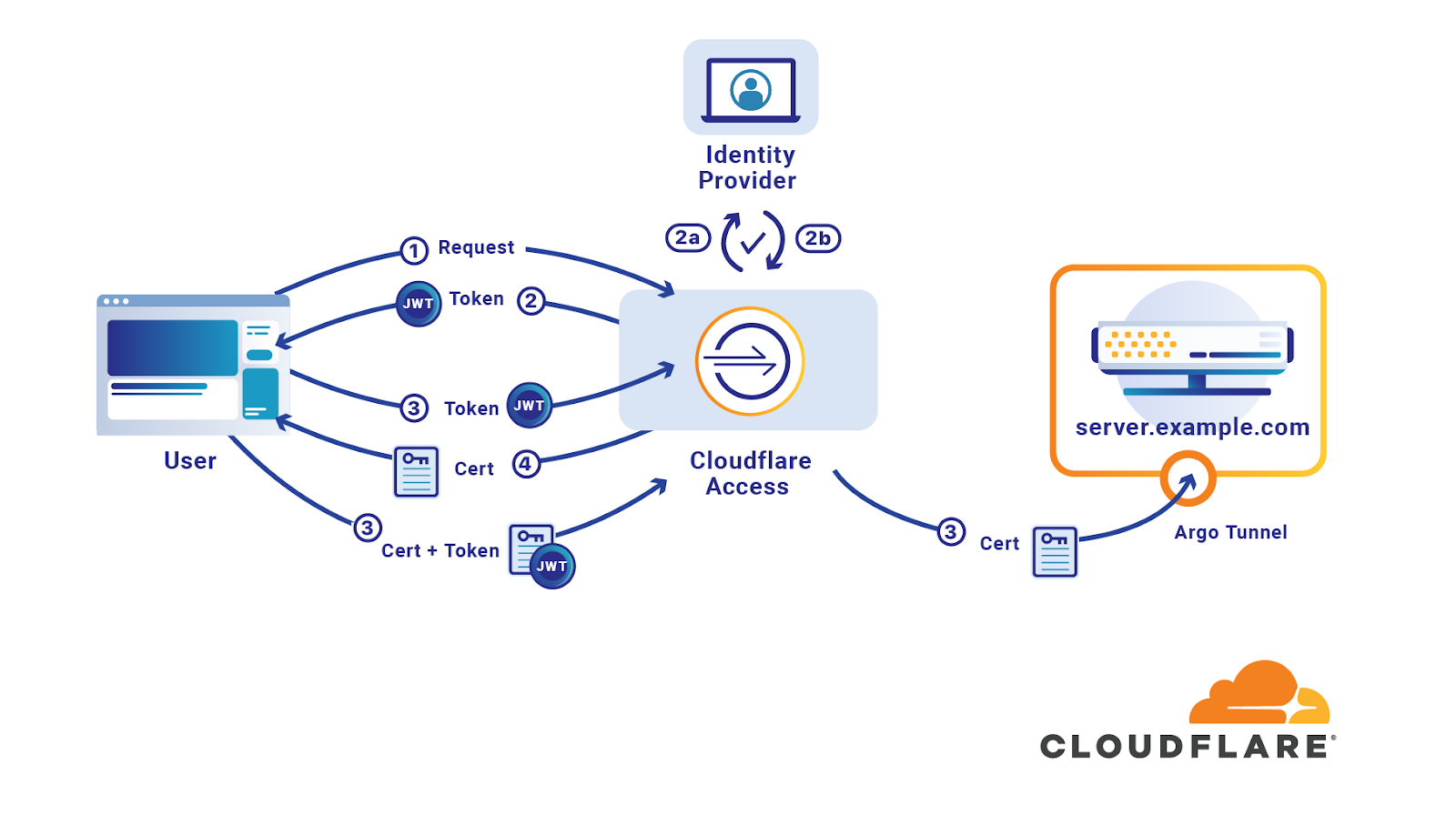
SSH connection setting method for Windows (when the PFM - RM host is running Windows and the monitored host is running UNIX)

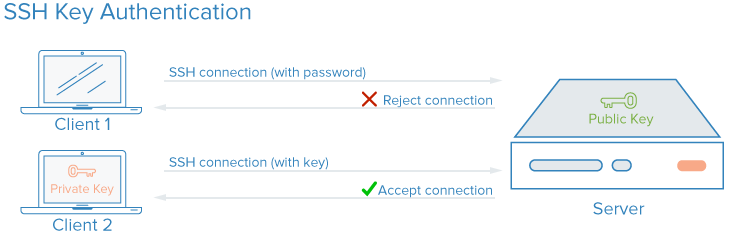
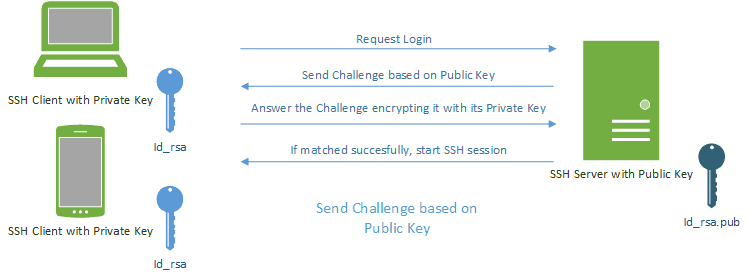
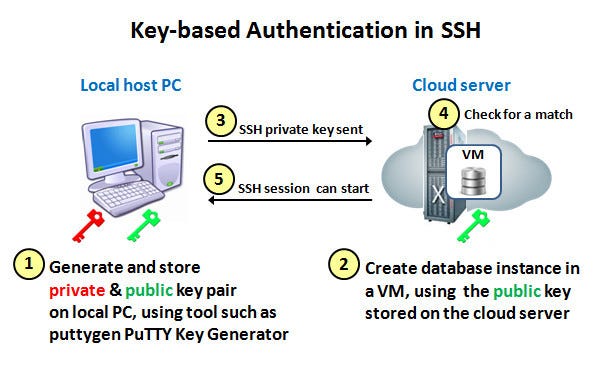
How to setup SSH key based authentication on Linux server - Reference Server - DYclassroom | Have fun learning :-)