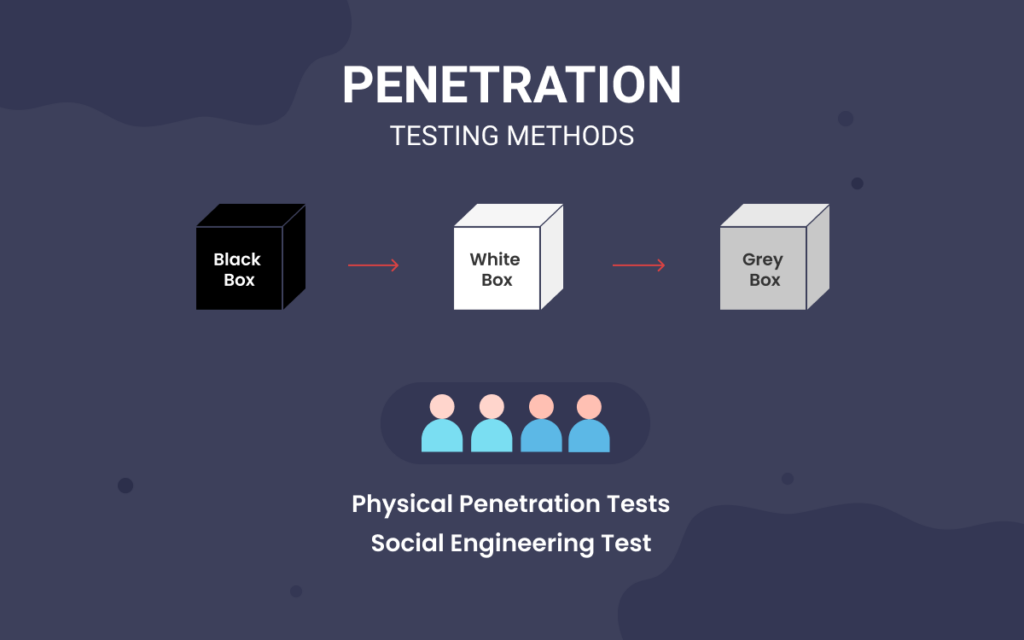
Learn Social Engineering Pen Testing with different Module – Infosavvy Cyber Security & IT Management Trainings

Amazon.com: Ethical Hacking: The Ultimate Beginner's Guide to Using Penetration Testing to Audit and Improve the Cybersecurity of Computer Networks, Including Tips on Social Engineering eBook : Evans, Lester: Kindle Store

Social Engineering Penetration Testing: Executing Social Engineering Pen Tests, Assessments and Defense: Watson, Gavin, Mason, Andrew, Ackroyd, Richard: 9780124201248: Amazon.com: Books




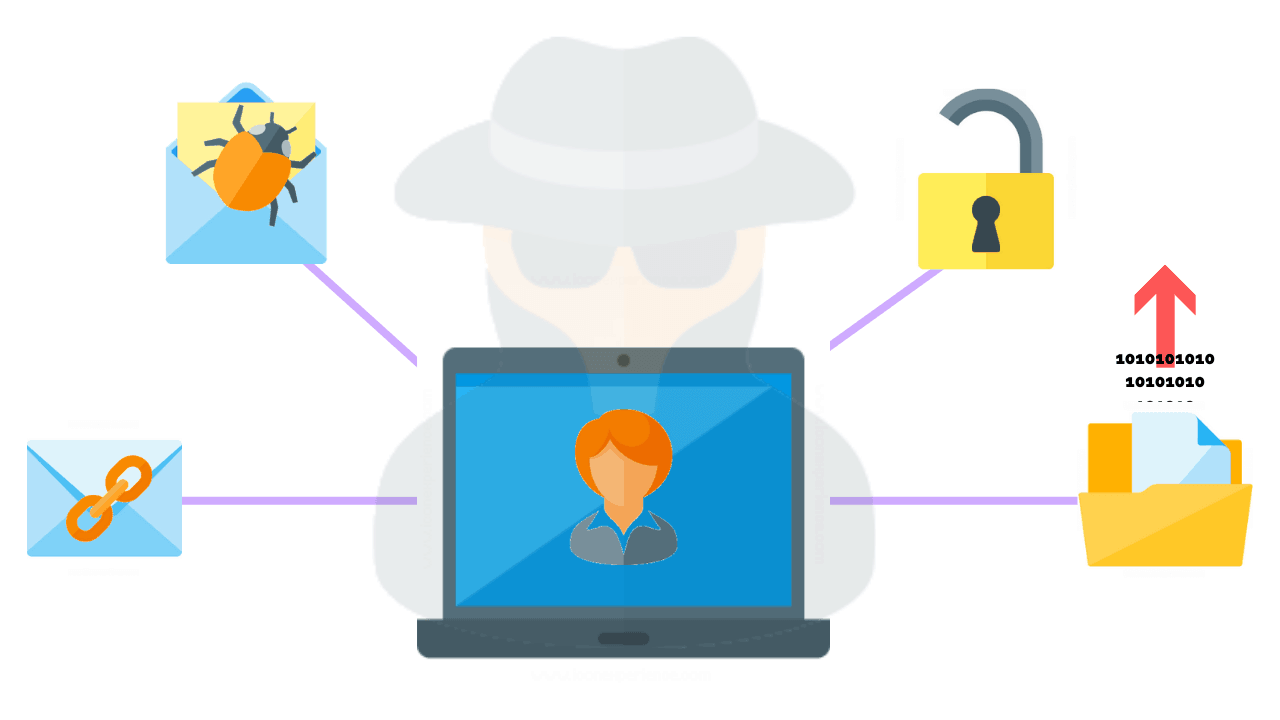


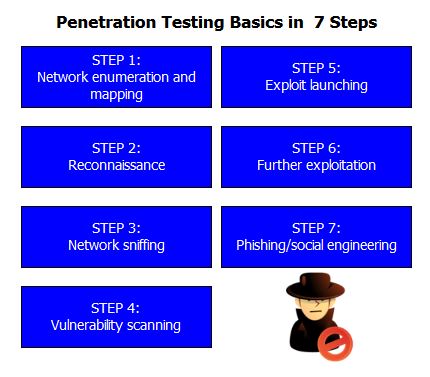

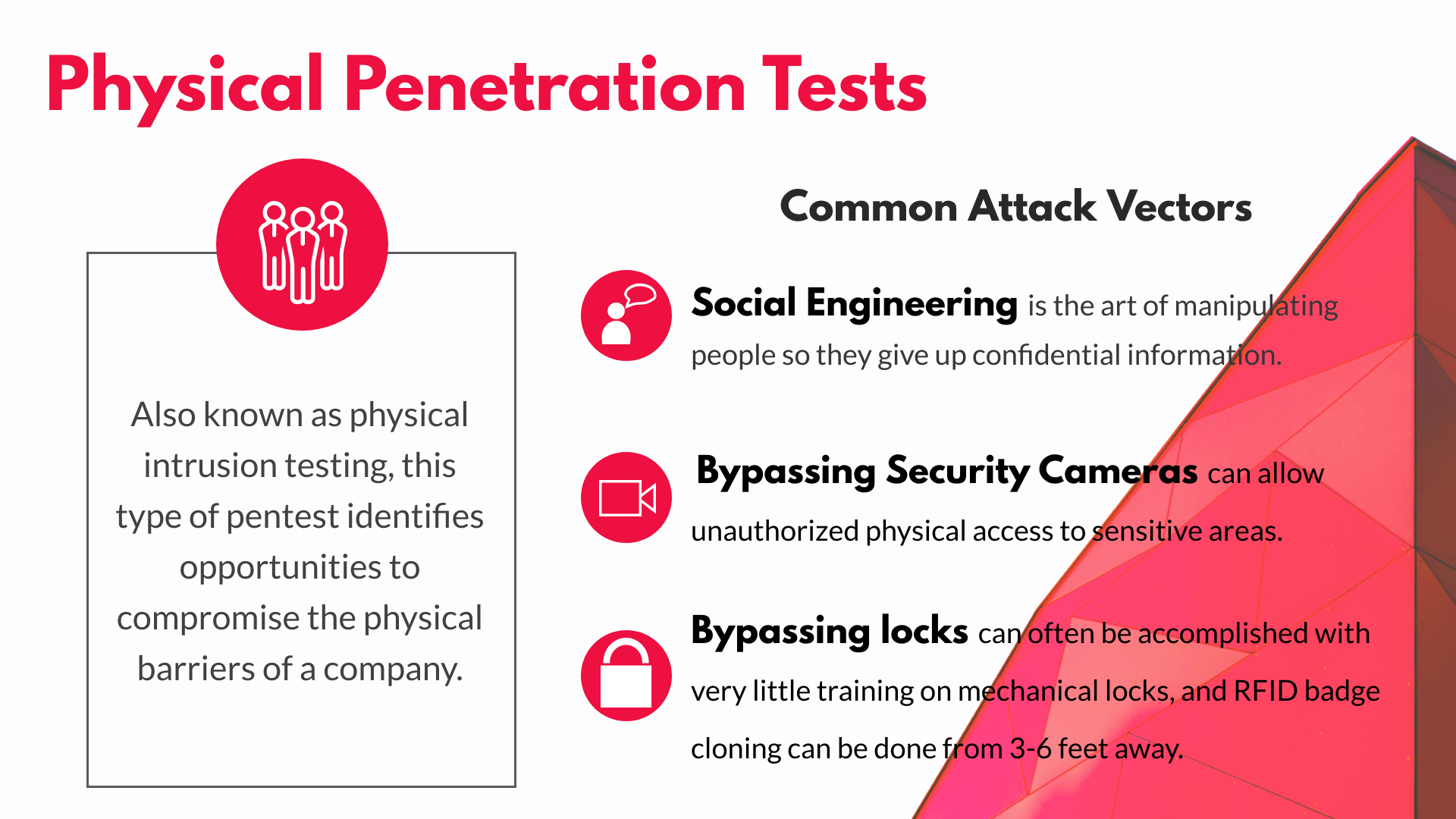



![Anatomy Of A Great Penetration Tester [Infographic] – eLearnSecurity Blog Anatomy Of A Great Penetration Tester [Infographic] – eLearnSecurity Blog](https://blog.elearnsecurity.com/wp-content/uploads/2019/02/Anatomy-Of-Penetration-Tester-Infographc-01.jpg)